Rolling code technology, also known as hopping code, has become an essential element in the modern world of secure communication, especially in remote keyless entry systems. From garage door openers to car key fobs, this technology prevents unauthorized access by ensuring that the transmitted signal changes every time. This article explores the origins of rolling code systems, how they work, and how they evolved into one of the most widely adopted cryptographic practices in consumer electronics.
In the 1980s, remote keyless entry systems began appearing in vehicles and garage doors. These early systems used fixed codes — static signals that, once learned or intercepted, could be replayed to gain unauthorized access. The simplicity of these systems made them highly vulnerable to “replay attacks.” Criminals could use simple radio scanners to record the fixed signal and retransmit it later to open a garage or unlock a car[1].
As vehicle theft and unauthorized entries increased, the need for a dynamic coding system became evident. Security experts began exploring methods to randomize or change the signal each time it was used, leading to the development of rolling codes.
The first significant commercial implementation of rolling code technology occurred in the early 1990s, led by companies such as Texas Instruments and Hella, in partnership with automotive manufacturers like Ford and Mercedes-Benz. The goal was to create a cryptographically secure method for transmitting access credentials that changed with each use and could not be easily duplicated[2].
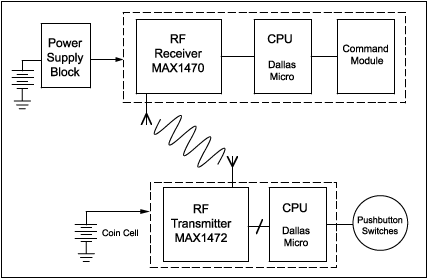
The key innovation was the use of a synchronized algorithm between the transmitter (e.g., key fob) and the receiver (e.g., vehicle system or garage opener). Each time the button was pressed, the transmitter sent a unique encrypted signal based on a shared secret key and a rolling counter. If the receiver recognized the signal within an expected range, it would authenticate the command and then update its internal counter.
The underlying mathematical principles drew from early work on pseudo-random number generators and cryptographic hashing. Rolling code systems typically use a one-way hash function such as the KeeLoq algorithm, which was developed by Microchip Technology and became widely licensed across the automotive industry in the mid-1990s[3].
Rolling code systems operate using a synchronized counter and an encryption algorithm. When a user presses a button on a remote control, the device sends an encrypted code that includes the counter value. The receiver decrypts the signal using the same shared algorithm and compares the counter value with its own. If the received value falls within a predefined range (window of acceptance), access is granted and the receiver counter is updated[4].
The system also includes mechanisms to handle signal loss or multiple button presses when out of range. For example, if a user accidentally presses the remote button multiple times while not near the receiver, the system allows a certain number of counter mismatches to maintain synchronization.
The major security advantage of rolling codes lies in their resistance to replay attacks. Even if an attacker captures a valid signal, it cannot be reused because the receiver will have already moved past that counter value.
Over the years, rolling code technology has become ubiquitous in car keyless entry systems, garage door openers, home security alarms, and industrial automation. Manufacturers such as Chamberlain, LiftMaster, and Somfy have adopted rolling code protocols to increase consumer security.
As security requirements grew, enhancements such as larger key lengths, improved synchronization algorithms, and integration with digital certificates were introduced. Some systems now combine rolling code with fixed-code identification to offer multi-factor authentication.
In addition, new wireless communication standards like Bluetooth Low Energy (BLE) and ultra-wideband (UWB) are increasingly incorporating rolling code logic to secure device pairing and access control in smart home and IoT devices.
Despite its strengths, rolling code systems are not invulnerable. Advanced relay attacks and jamming techniques have pushed researchers to explore even stronger security frameworks, including time-based tokens and biometric validation. Still, rolling code remains a foundational technology in the world of access control.
From its roots in the security shortcomings of early fixed-code systems, rolling code technology has evolved into a robust, widely implemented defense against digital intrusion. Its development in the early 1990s marked a turning point in the design of secure access systems. Today, as technology continues to advance, rolling code protocols are being adapted to new platforms, ensuring that the core principles of cryptographic rolling authentication remain vital in the fight against unauthorized access.